TACTICAL.OPERATIONS.CENTER
Advanced cybersecurity warfare protocols engineered for maximum operational efficiency and system domination.
100%
Success Rate
24/7
Support
50+
Clients
5+
Years Exp
Our Services
Expert cybersecurity solutions designed to protect your organization
Penetration Testing
Comprehensive security assessments to identify vulnerabilities in your systems and infrastructure.
- Web Application Testing
- Network Infrastructure
- Mobile Security
- Cloud Security
CTF Training
Expert-led training programs to enhance your CTF and security skills through hands-on experience.
- Beginner to Advanced
- Hands-on Labs
- Team Building
- Custom Programs
Security Consulting
Strategic guidance to strengthen your organization's security posture and compliance.
- Architecture Review
- Compliance Support
- Incident Response
- Risk Assessment
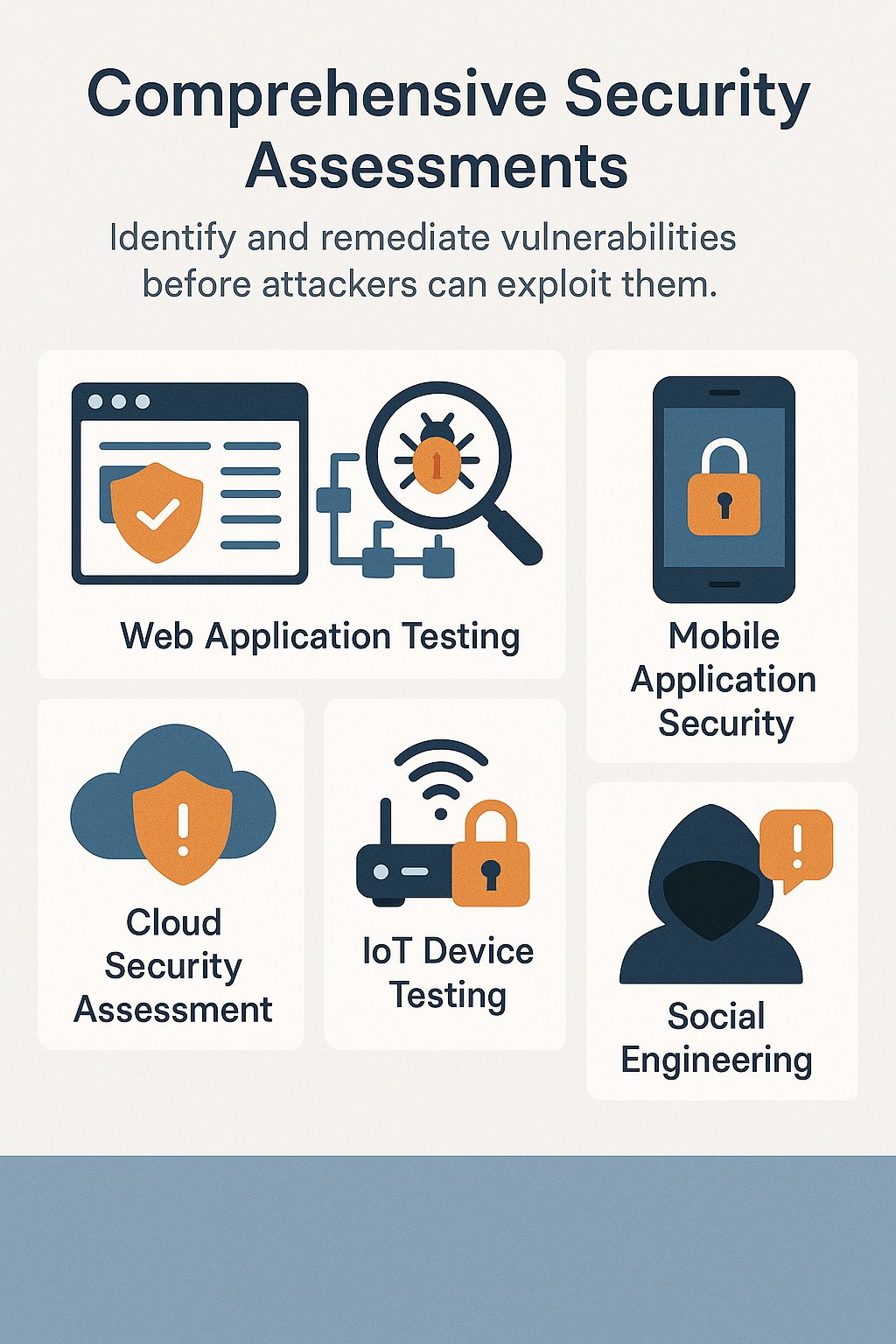
Comprehensive Security Assessments
Identify and remediate vulnerabilities before attackers can exploit them.
- Web Application Testing
- Network Infrastructure Testing
- Mobile Application Security
- Cloud Security Assessment
- IoT Device Testing
- Social Engineering
Expert-Led Security Training
Develop your cybersecurity skills through hands-on training and real-world scenarios.
- Beginner to Advanced Tracks
- Hands-on Lab Exercises
- Real-world Scenarios
- Custom Training Programs
- Team Building Workshops
- Certification Preparation
Strategic Security Guidance
Strengthen your organization's security posture with expert consulting services.
- Security Architecture Review
- Risk Assessment
- Compliance Consulting
- Incident Response Planning
- Security Program Development
- Policy & Procedure Review

Our Process
A systematic approach to securing your digital assets
1. Assessment
Comprehensive analysis of your current security posture
2. Planning
Strategic planning and custom solution development
3. Implementation
Expert execution of security measures and training
4. Monitoring
Ongoing support and continuous security monitoring
Ready to Secure Your Digital Assets?
Contact us today to discuss how we can help protect your organization.